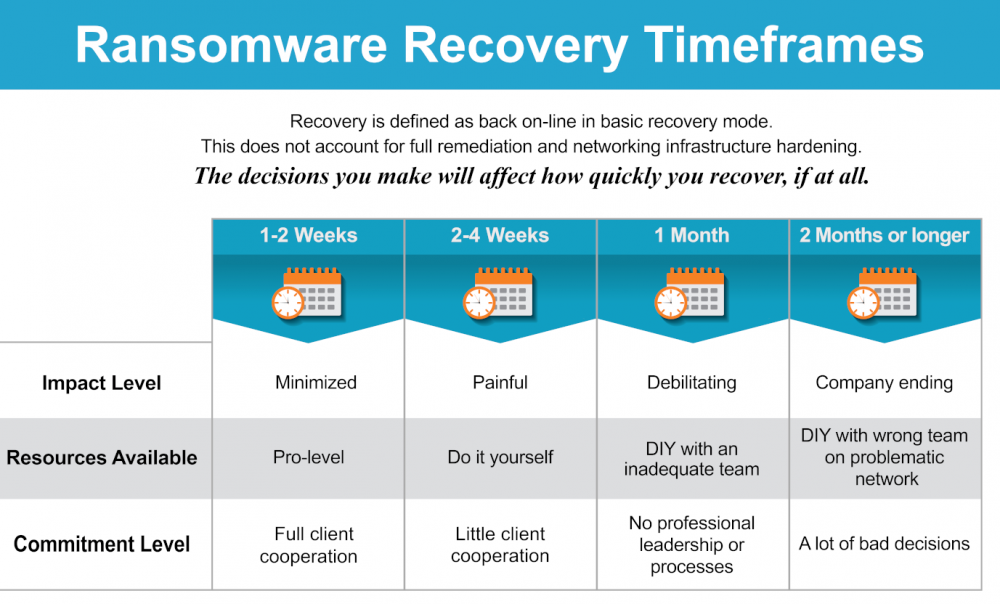
Ransomware recovery timeframes can vary widely. In very unusual situations, companies are only down for a day or two. In other unusual cases, it can take months. Most companies fall somewhere between the two to four week range, given their struggle with not knowing what they are doing. In 2022, under the right conditions, timeframes have compressed down to seven days for the return to service of the most vital elements of the infrastructure. Getting the tier two critical infrastructure back online averages around 14 days. It is important to reiterate that all situations vary, and these compressed timeframes presume an experienced ransomware recovery team, armed with the right tools, has been engaged early in the event.
For most victims, a ransomware recovery is their first introduction into a debilitating cyber-attack. Much time is lost just figuring out what to do, while being inundated with fear and uncertainty. In a well-managed ransomware recovery effort—being executed by an experienced team—a common time frame is one to two weeks. However, there are a tremendous number of variables to consider.
It is important to state that “recovery” is defined here as getting the IT system back online so the company can transact business. After the company is back online and operational, there’s typically several more weeks of work to be done making sure the IT management and security infrastructure is effectively more robust than before the ransomware attack.
Companies that have taken a few weeks or longer to get operational again, or are operating in severely degraded states, have not put the right team on the recovery process. What might have initially seemed like a budget-wise decision by an overly confident management and IT team, turns out to be horrible for revenue, profit and the value of the brand reputation, in terms of company valuation. In severe cases, a prolonged recovery effort leads to the failure of the victimized entity.
Variables of Ransomware Recovery Timeframes
So, what are the variables that will impact ransomware recovery timeframes? Here they are listed in order of importance and impact:
1. The most important factor to a fast recovery is having an experienced, and well-coordinated, team of experts utilizing proven tools and techniques for getting you back up and running. That team consists of:
a. A good insurance company (if you have one)
b. A good cyber breach experienced lawyer
c. A good incident response/digital forensics firm
d. A good ransomware recovery IT team, executing on a proven containment list
e. A company that has contacts within the FBI, Secret Service and other agencies that may be able to help
f. A good ransomware negotiator that can bring down the cost of your ransom, pay the ransom with bitcoin on your behalf, and help with the decryption process
g. (In some cases) A public relations firm to help mitigate your company’s brand damage
h. (Post recovery) A managed service provider that can provide sound security services to prevent future attacks
2. The type of ransomware you were infected with and the gang that victimized you.
a. Some ransomware variants are more effective at spreading throughout your entire system, while others are not so much.
b. Some ransomware variants delete or encrypt your backups so you can’t use them to recover.
c. Are the bad guys in your system, in full control and navigating around ready to cause you further trouble as you try to recover? Or was it just a dumb software robot that executed a simpler attack?
d. Is this an experienced, aggressive, ambitious gang that know how to create maximum pain and suffering? Or is it a newer, less sophisticated, bad actor that is licensing ransomware tools from more experienced technology criminals?
3. The size of your IT infrastructure.
a. Small systems are generally faster and easier to recover than large systems.
4. The pre-attack configuration of your IT infrastructure.
a. Systems that are mature and well managed make for faster recoveries.
b. Systems that are run on a shoestring budget, and exhibit the IT management challenges that go with that sort of situation, can be very problematic.
5. The size, experience level, and maturity of your IT team.
a. An effective IT team will execute much faster on their own, or in unison with an outside ransomware recovery team.